37+ entity boundary control class diagram
RFC 760 IENs 128 123 111 80 54 44 41 28 26 INTERNET PROTOCOL DARPA INTERNET PROGRAM PROTOCOL SPECIFICATION 1. Paragraph 3-97 contains proration examples.

Rapid Uml Solution Software Development Flow Chart Drawing Software
This set theory is defined by ambiguous boundaries.
. Test planning comprises of the following major tasks. This theory is a class of those sets having sharp boundaries. Update RasterUpdate a raster in an image service.
- External entities represent any entity that supplies or receive information. The description of Node Connectivity Diagram and Information Exchange Matrix are removed because they are not generally applicable. Deriving the design from the requirements using the entity-control-boundary approach.
One of the first uses of the term protocol in a data-commutation context occurs in a memorandum entitled A Protocol for Use in the NPL Data Communications Network written by Roger Scantlebury and Keith Bartlett in April 1967. On the ARPANET the starting point for host-to-host communication in 1969 was the 1822 protocol which defined. Writing use cases in templates devised by various vendors or experts is a common industry.
In this theory there is no uncertainty about the boundarys location of a set. Approved boundary protection devices eg routers firewalls mediate communications ie information flows between unclassified non-national security systems and external networks. Improve Airport Erosion Control 1 Stand-alone projects for erosion control blast pads installation of sod etc are eligible to the extent that they are needed to protect AIP eligible facilities.
It is also called context level DFD. To govern the test. 2 The ADO will determine the method of proration.
Crime Control ActReporting of Child Abuse. Department of Labor. The exceededTransferLimit property is now included in the JSON response when paging through a query result with the resultOffset and resultRecordCount.
The feature service layer Query operation supports the returnTrueCurves historicMoment and sqlFormat parameters. 29 What is mean by level-0 Data flow diagram. This set theory is defined by exact boundaries only 0 and 1.
Indias territorial limit extends towards the sea. NAME UNIVERSITY ROLL NO CLASS Sanjana Agarwal 1461330107 BCA 6sem 3rd year Saloni Lohiya 1461330106 BCA 6sem 3rd year Sachin Padhlani 1461330060 BCA 6sem 3rd year Rohit Singh 1461330059 BCA 6sem 3rd year Ravi Negi 1461330058 BCA 6sem 3rd year. To fix the scope and the number of risks and ascertain the goals of testing.
HTTP has been in use by the World-Wide Web global information initiative since 1990. Planning and Control. An example of a 1N relationships is a department has many employees each employee is assigned to one department A many-to-many MN relationship sometimes called non-specific is when for one instance of entity A there are zero one or many instances of entity B and for one instance of entity B there 21 Hospital Management System are zero.
The feature service layer Query operation supports the returnTrueCurves parameter. Explain the tasks involved in planning and control. It includes all kind of activities that are done to develop and deliver the software product.
Query Image ServiceQuery an image service resource by applying a specified filter. This control enhancement is required for organizations processing storing or transmitting Controlled Unclassified Information CUI. This theory is a class of those sets having un-sharp boundaries.
For example attributes footprints or. Crime Control ActRequirement for Background Checks. Software scope is a well-defined boundary.
The first version of HTTP referred to as HTTP09 was a simple protocol for raw data transfer. 7 Enter in the name of the entity whose index is used in the clause. It portrays the.
The mainland extends Kanniyakumari Cape Caverian and 376 N Indira col Jammu and Kashmir and longitudes 687 E Dwarka Gujarat and 9725 E Sadiya Arunachal Pradesh. Highest abstraction level is called Level 0 of DFD. Evaluating exit criteria and Reporting.
In most cases when using this clause format the index used would be a CPI-U Index and the Contracting Officer would enter the US. RFC 2068 HTTP11 January 1997 1 Introduction 11 Purpose The Hypertext Transfer Protocol HTTP is an application-level protocol for distributed collaborative hypermedia information systems. INTRODUCTION 11Motivation The Internet Protocol is designed for use in interconnected systems of packet-switched computer communication networks.
ST OT IM. Entity Relationship Diagrams and Decision tables. There are many ways to write a use case in text from use case brief casual outline to fully dressed etc and with varied templates.
A reduction in erosion. Query BoundaryCalculate the boundary geometry and its area of coverage of the image service. The bullet Class Models is changed to Logical Data Model or Class Model and the description generalized with class model introduced as a specific type of Logical Data Model.
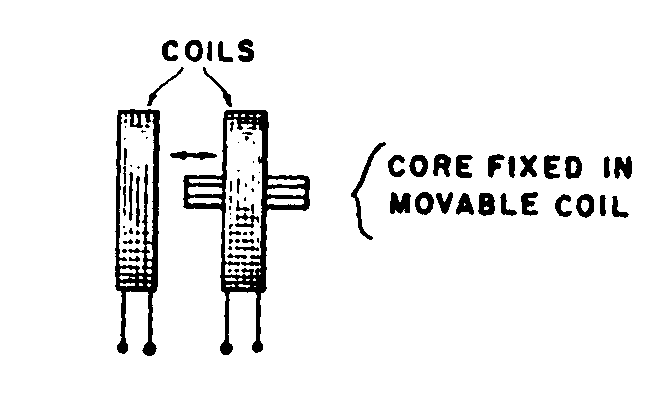
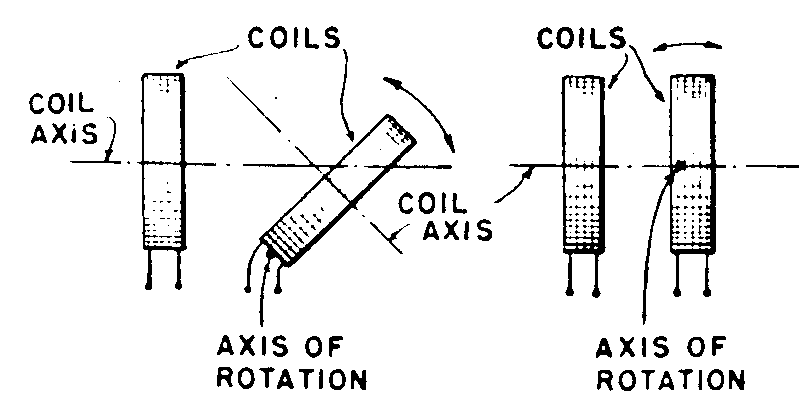
Class Definition For Class 336 Inductor Devices
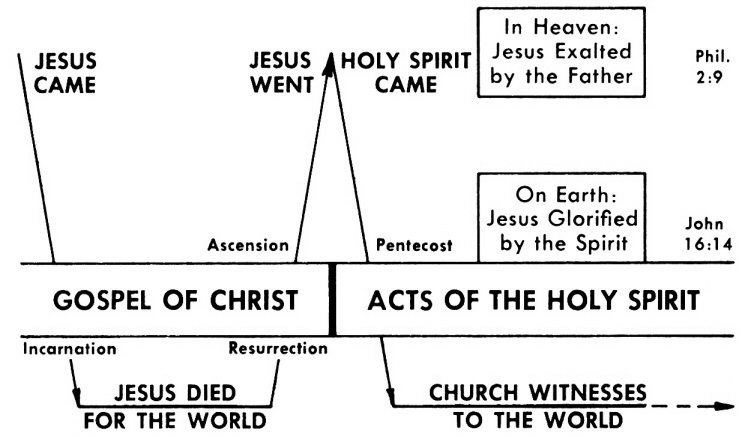
Acts 13 Commentary Precept Austin
2

Class Definition For Class 336 Inductor Devices
2
2

Computer Science It Study Notes And Projects Notes

Sequencediagram Carrentalbooking Sequence Diagram Class Diagram Diagram
Acts 2 Commentary Precept Austin

Class Definition For Class 336 Inductor Devices
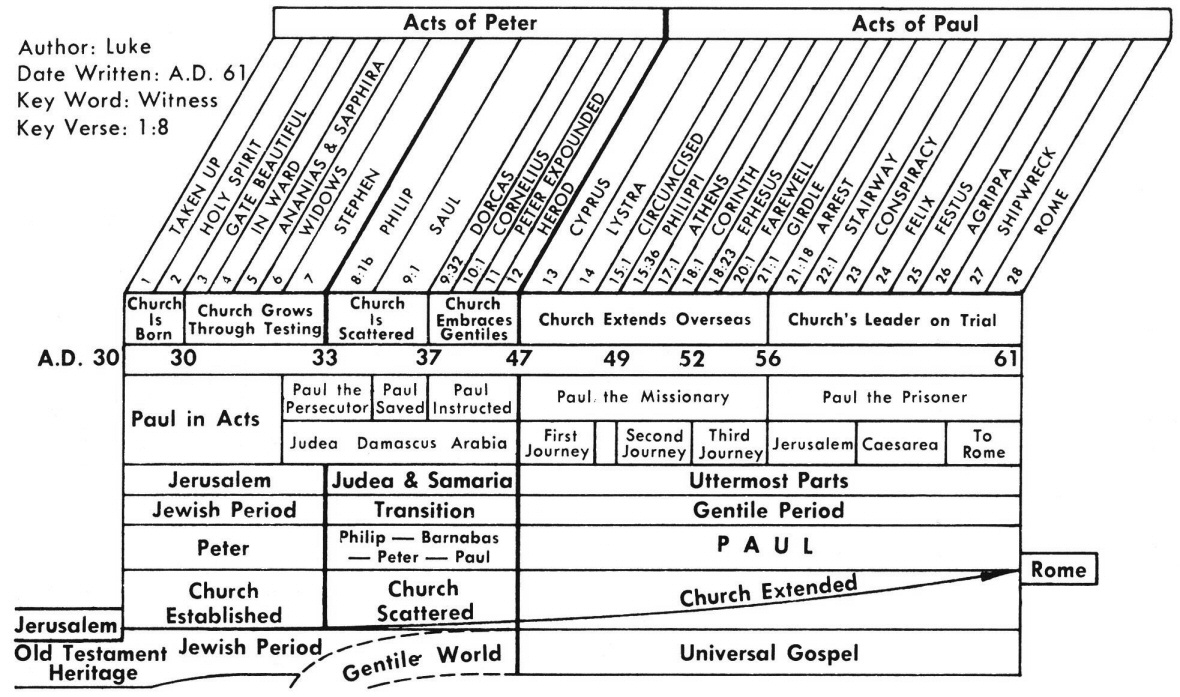
Acts 2 Commentary Precept Austin
2
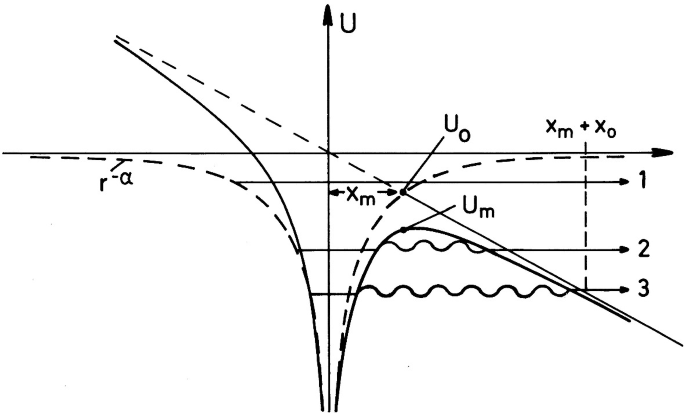
Hot Matter From High Power Lasers Springerlink
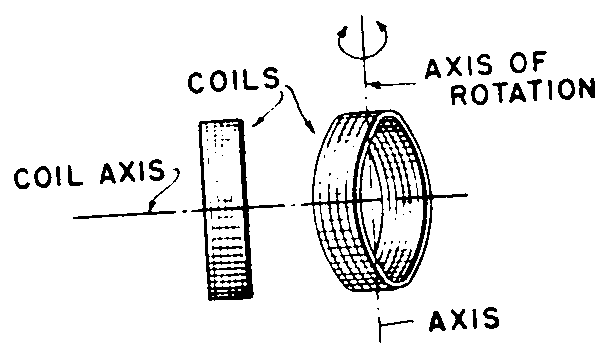
Class Definition For Class 336 Inductor Devices
2

Pdf Handbook On Chemical And Biological Waste Management

Rapid Uml Solution Software Development Use Case Diagram